Technologies
$20 MILLION/Kg: The Resource Worth a Trip to the Moon
Technologies
Today’s NYT Strands Hints, Answers and Help for Jan. 9 #677
Here are hints and answers for the NYT Strands puzzle for Jan. 9, No. 677.
Looking for the most recent Strands answer? Click here for our daily Strands hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle, Connections and Connections: Sports Edition puzzles.
Today’s NYT Strands puzzle is a fun topic — but one of the answers describes something I’ve never heard of before. Also, some of the answers are difficult to unscramble, so if you need hints and answers, read on.
I go into depth about the rules for Strands in this story.
If you’re looking for today’s Wordle, Connections and Mini Crossword answers, you can visit CNET’s NYT puzzle hints page.
Read more: NYT Connections Turns 1: These Are the 5 Toughest Puzzles So Far
Hint for today’s Strands puzzle
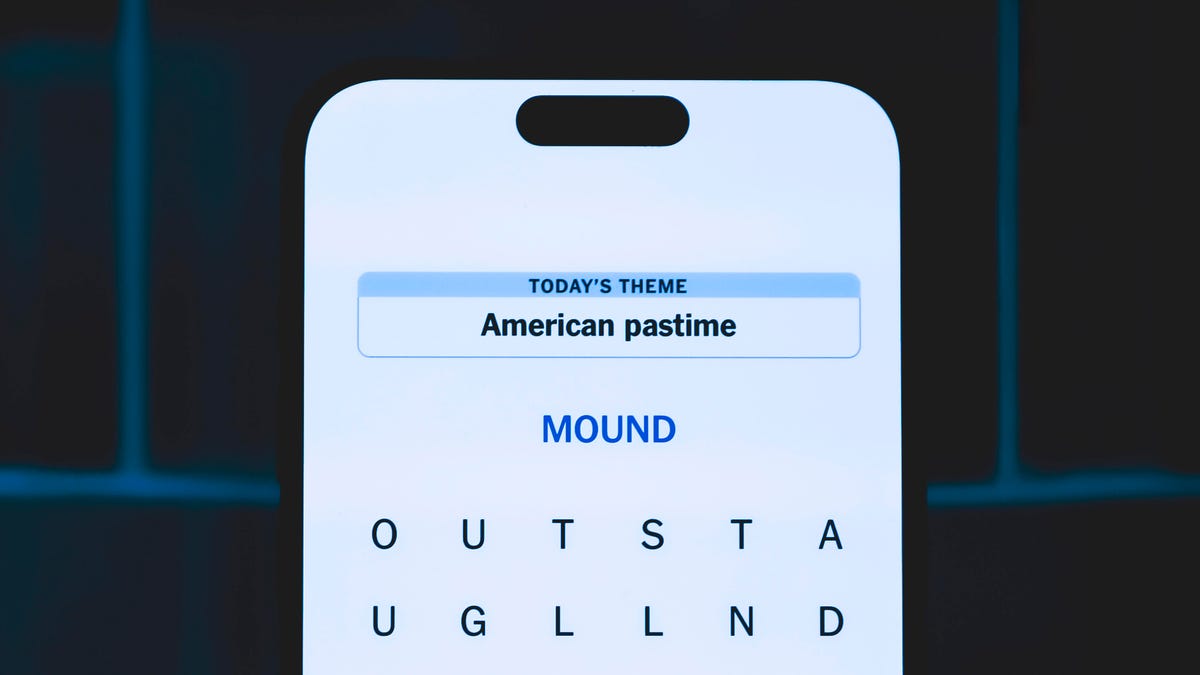
Today’s Strands theme is: For cubs fans.
If that doesn’t help you, here’s a clue: Like Gentle Ben.
Clue words to unlock in-game hints
Your goal is to find hidden words that fit the puzzle’s theme. If you’re stuck, find any words you can. Every time you find three words of four letters or more, Strands will reveal one of the theme words. These are the words I used to get those hints but any words of four or more letters that you find will work:
- LAIR, RAIL, CROP, LAID, BALD, DEAN, BROW, DIZZY
Answers for today’s Strands puzzle
These are the answers that tie into the theme. The goal of the puzzle is to find them all, including the spangram, a theme word that reaches from one side of the puzzle to the other. When you have all of them (I originally thought there were always eight but learned that the number can vary), every letter on the board will be used. Here are the nonspangram answers:
- BLACK, BROWN, GRIZZLY, PANDA, POLAR, SPECTACLED (That last one is the one I’ve never heard of! But it’s real!)
Today’s Strands spangram
Today’s Strands spangram is BEARSINMIND. To find it, start with the B that’s five rows to the right and three letters down, then wind up, over and down the whole far-right row.
Don’t miss any of our unbiased tech content and lab-based reviews. Add CNET as a preferred Google source.
Toughest Strands puzzles
Here are some of the Strands topics I’ve found to be the toughest.
#1: Dated slang. Maybe you didn’t even use this lingo when it was cool. Toughest word: PHAT.
#2: Thar she blows! I guess marine biologists might ace this one. Toughest word: BALEEN or RIGHT.
#3: Off the hook. Again, it helps to know a lot about sea creatures. Sorry, Charlie. Toughest word: BIGEYE or SKIPJACK.
Technologies
Today’s NYT Mini Crossword Answers for Friday, Jan. 9
Here are the answers for The New York Times Mini Crossword for Jan. 9.

Looking for the most recent Mini Crossword answer? Click here for today’s Mini Crossword hints, as well as our daily answers and hints for The New York Times Wordle, Strands, Connections and Connections: Sports Edition puzzles.
Need some help with today’s Mini Crossword? The Across clues were kind of tough today. Read on for all the answers. And if you could use some hints and guidance for daily solving, check out our Mini Crossword tips.
If you’re looking for today’s Wordle, Connections, Connections: Sports Edition and Strands answers, you can visit CNET’s NYT puzzle hints page.
Read more: Tips and Tricks for Solving The New York Times Mini Crossword
Let’s get to those Mini Crossword clues and answers.
Mini across clues and answers
1A clue: Question in a late-night text
Answer: YOUUP
6A clue: Plentiful
Answer: AMPLE
7A clue: Saint ___ and Nevis (Caribbean nation)
Answer: KITTS
8A clue: Baby-bringing bird
Answer: STORK
9A clue: Take care of the tab
Answer: PAY
Mini down clues and answers
1D clue: Himalayan herbivores
Answer: YAKS
2D clue: Fail to include
Answer: OMIT
3D clue: «High five!»
Answer: UPTOP
4D clue: The «U» of UV rays
Answer: ULTRA
5D clue: Annoying to deal with
Answer: PESKY
Don’t miss any of our unbiased tech content and lab-based reviews. Add CNET as a preferred Google source.
Technologies
I Got Up Close and Personal With Boston Dynamics’ New Atlas Robot
Before Atlas takes its first steps into the world of work later this year, I found myself face-to-face with CES 2026’s most talked-about robot on the show floor.
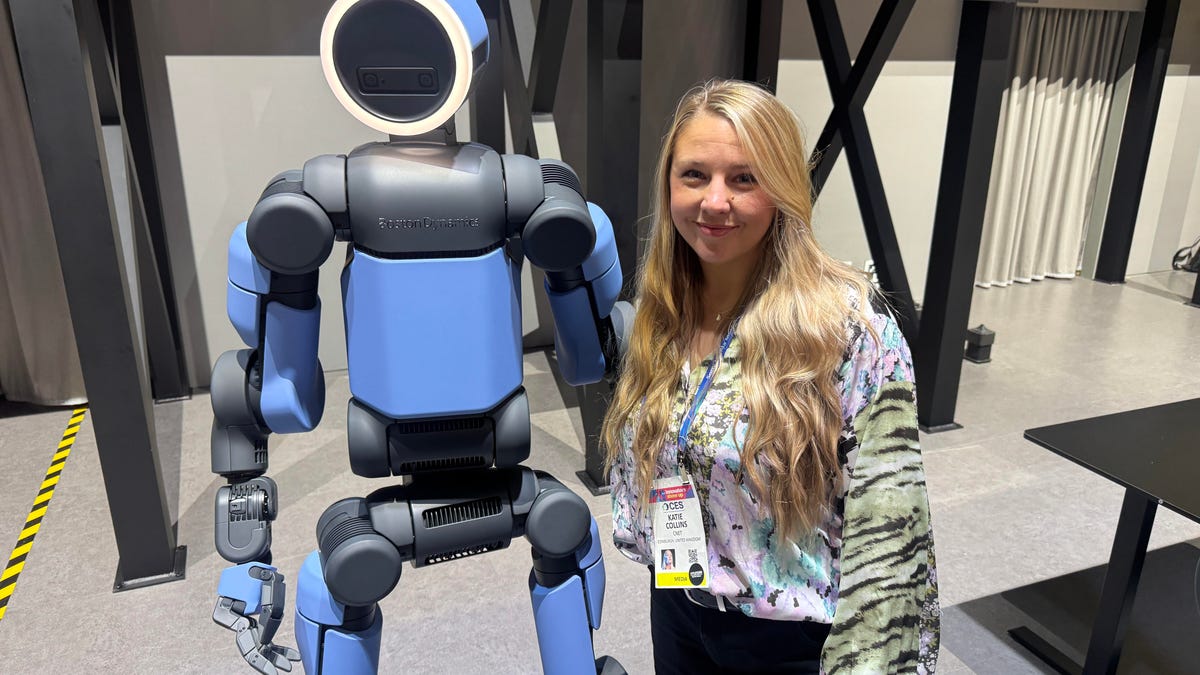
When I say that I went hands-on with the new Boston Dynamics Atlas robot, I mean that I actually held hands with it. This humanoid robot, which CNET just awarded the Best Robot of CES Award, is one of the most advanced in the world, and I couldn’t pass up the opportunity to get up close and personal with it.
This product version of the robot, which is set to be shipped to Hyundai factories imminently to start working, has been the talk of CES this year. The specific Atlas robot I encountered was a static model that wasn’t turned on or fully operational. Our interactions were, therefore, sadly one-sided. Still, I ran my hands over its soft-touch plastic shell and gently prodded at its finger joints, wondering how it would feel if they gripped me back.
People tend to have varying feelings about humanoid robots — understandable given that they are built to some degree in our image, while also usually being stronger than us, with «brains» that we don’t fully understand. Atlas definitely evokes contradictory emotions for me — even more so when I stood face-to-face with it.
I’m in awe of the engineering, a little fearful of its capabilities, hesitant about what it could mean for the future of humanity and charmed by its design and styling. The periwinkle blue iteration of Atlas that I met on the show floor at CES 2026 almost bears more resemblance to a Dyson product than it does the industrial robots that defined Boston Dynamics’ early days, when it was best known for its work with DARPA.
«There’s a lot of really specific things about this robot that probably look a little weird,» said Zachary Jackowski, Boston Dynamics VP and general manager of Atlas. He pointed to the legs, which he described as «like nothing anyone else was doing.»
Atlas’ thighs are narrow set and in line with the torso, while the calves are wider set, attached to their upper counterparts with a circular joint. This robot is, in fact, all subtle curves and soft lines. There are no harsh edges or stark angles.
During a year when CES has been flooded with humanoid robots, Atlas definitely does stand out due to its design. It appears both less classically human and less industrial than some of its peers, while also lacking the often intimidating, featureless faces they tend to exhibit. Instead, it has two low-set cameras resembling eyes placed where you’d usually expect a mouth to be. Its face is a perfect flat circle, defined by an LED halo that gives it a somewhat Pixar lamp effect.
I asked Jackowski why Boston Dynamics decided to skew so relatively unhuman with this version of its humanoid. «Well, it’s not a human,» he said. «It projects the wrong first impression about a robot to have it pretend to be something that it’s not.»
Particularly in the early days of humanoids, he added, robots won’t have anything like human-like intelligence. People should look at it and see it for what it is — a tool for performing tasks safely and efficiently.
In fact, most of the design decisions were made to keep Atlas as simple, scalable and safe as possible, Jackowski said. I remark that there’s some irony in thinking of a humanoid robot as simple, given the complexity of the technology and development process to bring Atlas to life.
The key to making it simple, Jackowski said, is having a strong enough grasp of the technology to «accomplish the complex thing of building a humanoid robot,» but then being able to take it apart and understand that you can use fewer computers and actuators in it while achieving the same results.
And it’s essential to Boston Dynamics that Atlas is perceived as simple. After all, it’s a general-purpose humanoid, which might eventually be sent far and wide to fulfil all manner of roles. Jackowski calls it the «ultimate generalist.»
Simplicity aside, there are aspects of Atlas that Jackowski believes set it apart from other humanoids at the show. «The repairability of this robot is crazy good,» he said. «The runtime is crazy good. The strength is unlike anything.»
From working in Hyundai’s manufacturing plants, Atlas’s job trajectory is to eventually graduate to many of the same industrial environments where Boston Dynamics’ Spot robot works, before moving to bussing tables in the service industry and eventually into the home. The robot will evolve between now and then, Jackowski said. However, this could be an early glimpse of the type of humanoid that will eventually be our housemate.
That’s some way away, though, which is probably for the best. As I gaze up at Atlas, which I’d guess is around the same height as my husband, my feeling is that, however impressive Atlas is, I’m still not ready for it to move in.
-

 Technologies3 года ago
Technologies3 года agoTech Companies Need to Be Held Accountable for Security, Experts Say
-

 Technologies3 года ago
Technologies3 года agoBest Handheld Game Console in 2023
-

 Technologies3 года ago
Technologies3 года agoTighten Up Your VR Game With the Best Head Straps for Quest 2
-

 Technologies4 года ago
Technologies4 года agoBlack Friday 2021: The best deals on TVs, headphones, kitchenware, and more
-

 Technologies4 года ago
Technologies4 года agoGoogle to require vaccinations as Silicon Valley rethinks return-to-office policies
-

 Technologies4 года ago
Technologies4 года agoVerum, Wickr and Threema: next generation secured messengers
-

 Technologies4 года ago
Technologies4 года agoOlivia Harlan Dekker for Verum Messenger
-

 Technologies4 года ago
Technologies4 года agoiPhone 13 event: How to watch Apple’s big announcement tomorrow
