Technologies
If You Use LastPass, You Need to Change All of Your Passwords ASAP
You’ll probably also want to find a different password manager, considering the severity of the latest LastPass data breach.

LastPass, one of the world’s most popular password managers, suffered a major data breach in December, putting customers’ online passwords at risk and endangering their personal data.
On Dec. 22, LastPass CEO Karim Toubba acknowledged in a blog post that a security incident the company first disclosed in August eventually led to an «unauthorized party» stealing customer account information and sensitive vault data. The breach is the latest in a lengthy and troubling string of security incidents involving LastPass that date back to 2011.
It’s also the most alarming.
An unauthorized party was able to gain access to unencrypted subscriber account information like LastPass usernames, company names, billing addresses, email addresses, phone numbers and IP addresses, according to Toubba. That same unauthorized party was also able to steal customer vault data, which includes unencrypted data like website URLs as well as encrypted data like the usernames and passwords for all of the sites customers have stored in their vaults.
If you’re a LastPass subscriber, the severity of this breach should have you looking for a different password manager, because your passwords and personal data are at serious risk of being exposed.
What should LastPass subscribers do?
The company didn’t specify how many users were affected by the breach, and LastPass didn’t respond to CNET’s request for additional comment on the breach. But if you’re a LastPass subscriber, you need to operate under the assumption that your user and vault data are in the hands of an unauthorized party with ill intentions. Though the most sensitive data is encrypted, the problem is that the threat actor can run «brute force» attacks on those stolen local files. LastPass estimates it would take «millions of years» to guess your master password — if you’ve followed its best practices.
If you haven’t — or if you just want total peace of mind — you’ll need to spend some serious time and effort changing your individual passwords. And while you’re doing that, you’ll probably want to transition away from LastPass, too.
With that in mind, here’s what you need to do right now if you’re a LastPass subscriber:
1. Find a new password manager. Given LastPass’ history with security incidents and considering the severity of this latest breach, now’s a better time than ever to seek an alternative.
2. Change your most important site-level passwords immediately. This includes passwords for anything like online banking, financial records, internal company logins and medical information. Make sure these new passwords are strong and unique.
3. Change every single one of your other online passwords. It’s a good idea to change your passwords in order of importance here too. Start with changing the passwords to accounts like email and social media profiles, then you can start moving backward to other accounts that may not be as critical.
4. Enable two-factor authentication wherever possible. Once you’ve changed your passwords, make sure to enable 2FA on any online account that offers it. This will give you an added layer of protection by alerting you and requiring you to authorize each login attempt. That means even if someone ends up obtaining your new password, they shouldn’t be able to gain access to a given site without your secondary authenticating device (typically your phone).
5. Change your master password. Though this doesn’t change the threat level to the stolen vaults, it’s still prudent to help mitigate the threats of any potential future attack — that is, if you decide you want to stay with LastPass.
LastPass alternatives to consider
- Bitwarden: CNET’s top password manager is a highly secure and open-source LastPass alternative. Bitwarden’s free tier allows you to use the password manager across an unlimited number of devices across device types. Read our Bitwarden review.
- 1Password: Another excellent password manager that works seamlessly across platforms. 1Password doesn’t offer a free tier, but you can try it for free for 14 days.
- iCloud Keychain: Apple’s built-in password manager for iOS, iPadOS and MacOS devices is an excellent LastPass alternative available to Apple users at no additional cost. iCloud Keychain is secure and easy to set up and use across all of your Apple devices. It even offers a Windows client, too, with support for Chrome and Edge browsers.
How did it come to this?
In August 2022, LastPass published a blog post written by Toubba saying that the company «determined that an unauthorized party gained access to portions of the LastPass development environment through a single compromised developer account and took portions of source code and some proprietary LastPass technical information.»
At the time, Toubba said that the threat was contained after LastPass «engaged a leading cybersecurity and forensics firm» and implemented «enhanced security measures.» But that blog post would be updated several times over the following months as the scope of the breach gradually widened.
On Sept. 15, Toubba updated the blog post to notify customers that the company’s investigation into the incident had concluded.
«Our investigation revealed that the threat actor’s activity was limited to a four-day period in August 2022. During this timeframe, the LastPass security team detected the threat actor’s activity and then contained the incident,» Toubba said. «There is no evidence of any threat actor activity beyond the established timeline. We can also confirm that there is no evidence that this incident involved any access to customer data or encrypted password vaults.»
Toubba assured customers at the time that their passwords and personal data were safe in LastPass’s care.
However, it turned out that the unauthorized party was indeed ultimately able to access customer data. On Nov. 30, Toubba updated the blog post once again to alert customers that the company «determined that an unauthorized party, using information obtained in the August 2022 incident, was able to gain access to certain elements of our customers’ information.»
Then, on Dec. 22, Toubba issued a lengthy update to the blog post outlining the unnerving details regarding precisely what customer data the hackers were able to access in the breach. It was then that the full severity of the situation finally came to light and the public found out that LastPass customers’ personal data was in the hands of a threat actor and all of their passwords were at serious risk of being exposed.
Still, Toubba assured customers who follow LastPass’s best practices for passwords and have the latest default settings enabled that no further action on their part is recommended at this time since their «sensitive vault data, such as usernames and passwords, secure notes, attachments, and form-fill fields, remain safely encrypted based on LastPass’ Zero Knowledge architecture.»
However, Toubba warned that those who don’t have LastPass’s default settings enabled and don’t follow the password manager’s best practices are at greater risk of having their master passwords cracked. Toubba suggested that those users should consider changing the passwords of the websites they have stored.
What does all of this mean for LastPass subscribers?
The initial breach ended up allowing the unauthorized party to access sensitive user account data as well as vault data, which means that LastPass subscribers should be extremely concerned for the integrity of the data they have stored in their vaults and should be questioning LastPass’s capacity to keep their data safe.
If you’re a LastPass subscriber, an unauthorized party may have access to personal information like your LastPass username, email address, phone number, name and billing address. IP addresses used when accessing LastPass were also exposed in the breach, which means that the unauthorized party could also see the locations from which you used your account. And because LastPass doesn’t encrypt users’ stored website URLs, the unauthorized party can see all of the websites for which you have login information saved with the password manager (even if the passwords themselves are encrypted).
Information like this gives a potential attacker plenty of ammunition for launching a phishing attack and socially engineering their way to your account passwords. And if you have any password reset links stored that may still be active, an attacker can easily go ahead and create a new password for themselves.
LastPass says that encrypted vault data like usernames and passwords, secure notes and form-filled data that was stolen remains secured. However, if an attacker were to crack your master password at the time of the breach, they would be able to access all of that information, including all the usernames and passwords to your online accounts. If your master password wasn’t strong enough at the time of the breach, your passwords are especially at risk of being exposed.
Changing your master password now will, unfortunately, not help solve the issue because the attackers already have a copy of your vault that was encrypted using the master password you had in place at the time of the breach. This means the attackers essentially have an unlimited amount of time to crack that master password. That’s why the safest course of action is a site-by-site password reset for all of your LastPass-stored accounts. Once changed at the site level, that would mean the attackers would be getting your old, outdated passwords if they managed to crack the stolen encrypted vaults.
For more on staying secure online, here are data privacy tips digital security experts wish you knew and browser settings to change to better guard your information.
Technologies
Apple to Build the Mac Mini in the United States for the First Time
Apple will begin manufacturing the wee desktop computer in Houston later this year.

Houston, we have some production. Apple announced Tuesday that it will be making its Mac Mini desktop computer in the US for the first time, shifting some manufacturing from its Asian plants, and will also increase AI server production at its existing Houston facility.
The California-based tech giant also said it will open the Advanced Manufacturing Center, a 20,000-square-foot facility where students, supplier employees and businesses will receive hands-on training in making Apple products, in the same city.
In its statement, Apple said the new Mac Mini production and increased AI server production will create thousands of jobs.
The Mac Mini will be manufactured at a 220,000-square-foot facility in North Houston. The other main building at that site is where Apple makes AI servers. The new Advanced Manufacturing Center will also be built at that location. The buildings are owned by Foxconn, the Chinese manufacturing giant that Apple initially partnered with in 2000 to produce the iMac.
Sabih Khan, Apple’s chief operating officer, said there will still be Mac Mini production in Asia after the Houston plant is up and running, according to a Wall Street Journal report.
By beginning Mac Mini production in the US, Apple is furthering its pledge to invest $600 billion in the US over four years. That promise, made last August, was in response to pressure from President Donald Trump’s administration to increase manufacturing in the US and to avoid Trump-imposed tariffs.
Apple also said it is sourcing more than 20 billion chips from 24 US factories, and that, by the end of 2026, every new iPhone and Apple Watch will have cover glass made at Corning’s facility in Harrodsburg, Kentucky.
CEO Tim Cook said his company is «deeply committed to the future of American manufacturing,» with production of the Mac Mini marking one step toward that commitment.
The Mac Mini, which initially went on sale in 2005 — CNET was there from the beginning — is the cheapest of the Apple desktops ($599 at the Apple store). It’s known as a BYODKM, an acronym coined by the late Apple co-founder Steve Jobs that stands for «Bring Your Own Display, Keyboard, Mouse.» In other words, the Mac Mini — only 5 inches long and 5 inches wide — comes without those peripherals, making it cheaper for those who already have them.
«The Mini can fit in your hand and be everything from an everyday home office computer to a full-on professional content-creation machine,» CNET’s Joshua Goldman wrote in his review of the latest model in 2024.
Goldman also said the Mac Mini is a «perfect pairing» with Apple Intelligence, the company’s AI system that is integrated with iPhones, iPads and Macs.
Market research firm Consumer Intelligence Research Partners estimates that the Mini accounts for less than 5% of its global Mac sales, according to the WSJ report.
Apple will also ramp up production of its AI servers. The company said manufacturing is ahead of schedule, months after beginning production in October. The servers are used in Apple data centers around the US.
Technologies
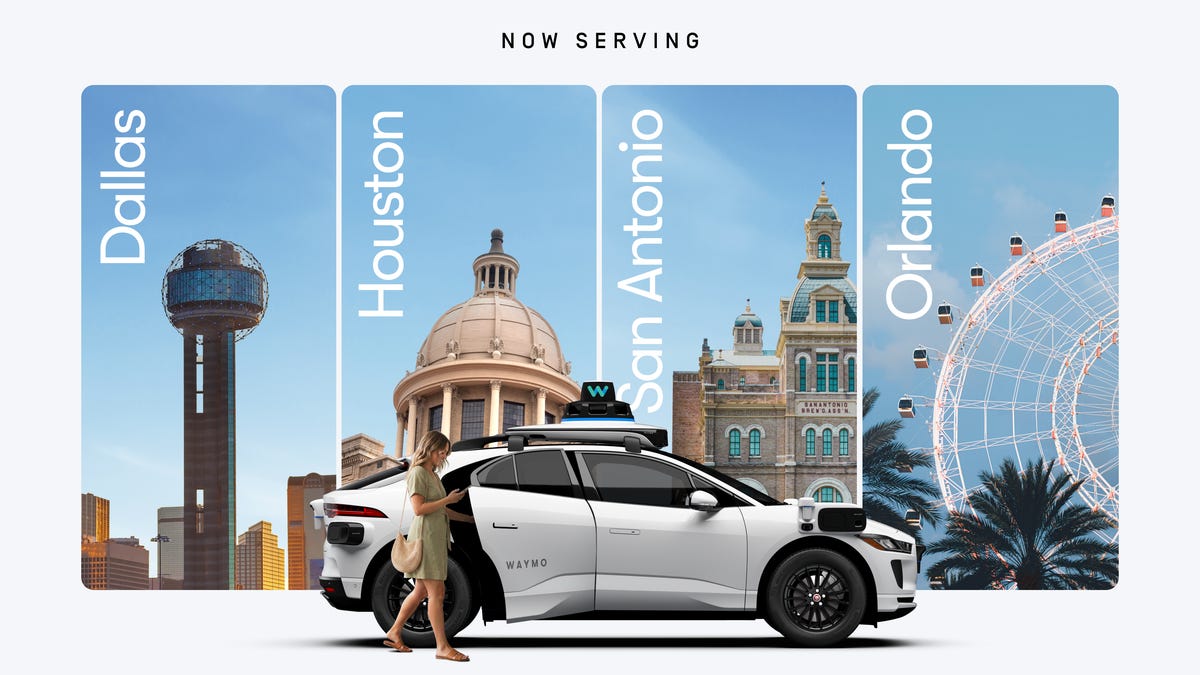
Waymo’s Autonomous Ride Service Expands to 4 New Cities
The company has doubled its operating area for robotaxi services over the past several months.
Technologies
Today’s NYT Connections Hints, Answers and Help for Feb. 25, #990
Here are some hints and the answers for the NYT Connections puzzle for Feb. 25 #990.

Looking for the most recent Connections answers? Click here for today’s Connections hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle, Connections: Sports Edition and Strands puzzles.
Today’s NYT Connections puzzle is kind of tough. That purple category, once again, expects you to spot hidden words that are related to each other within four of the grid words. It’s fun once you see the answer, but tough to figure out on your own. Read on for clues and today’s Connections answers.
The Times has a Connections Bot, like the one for Wordle. Go there after you play to receive a numeric score and to have the program analyze your answers. Players who are registered with the Times Games section can now nerd out by following their progress, including the number of puzzles completed, win rate, number of times they nabbed a perfect score and their win streak.
Read more: Hints, Tips and Strategies to Help You Win at NYT Connections Every Time
Hints for today’s Connections groups
Here are four hints for the groupings in today’s Connections puzzle, ranked from the easiest yellow group to the tough (and sometimes bizarre) purple group.
Yellow group hint: What a parent should do for a child.
Green group hint: «____ my dear Watson.»
Blue group hint: Some go by Jim.
Purple group hint: Look for hidden words.
Answers for today’s Connections groups
Yellow group: Care for.
Green group: Elementary.
Blue group: Jameses.
Purple group: Ending in family words.
Read more: Wordle Cheat Sheet: Here Are the Most Popular Letters Used in English Words
What are today’s Connections answers?
The yellow words in today’s Connections
The theme is care for. The four answers are baby, foster, mother and nurse.
The green words in today’s Connections
The theme is elementary. The four answers are basic, key, primary and principal.
The blue words in today’s Connections
The theme is Jameses. The four answers are Brown, Cook, Dean and Harden.
The purple words in today’s Connections
The theme is ending in family words. The four answers are alkaline (line), Declan (clan), diatribe (tribe) and napkin (kin).
-

 Technologies3 года ago
Technologies3 года agoTech Companies Need to Be Held Accountable for Security, Experts Say
-

 Technologies3 года ago
Technologies3 года agoBest Handheld Game Console in 2023
-

 Technologies3 года ago
Technologies3 года agoTighten Up Your VR Game With the Best Head Straps for Quest 2
-

 Technologies4 года ago
Technologies4 года agoBlack Friday 2021: The best deals on TVs, headphones, kitchenware, and more
-

 Technologies5 лет ago
Technologies5 лет agoGoogle to require vaccinations as Silicon Valley rethinks return-to-office policies
-

 Technologies5 лет ago
Technologies5 лет agoVerum, Wickr and Threema: next generation secured messengers
-

 Technologies4 года ago
Technologies4 года agoOlivia Harlan Dekker for Verum Messenger
-

 Technologies4 года ago
Technologies4 года agoiPhone 13 event: How to watch Apple’s big announcement tomorrow