Technologies
More Than 4.4 Million Exposed in Credit Bureau TransUnion Breach: What to Know
The breach appears related to a wave of attacks on companies’ Salesforce databases.

Sensitive personal information belonging to 4.4 million customers, including their names and Social Security numbers, was exposed in a data breach on credit bureau TransUnion, in what is believed to be the latest in a string of attacks targeting companies’ Salesforce databases.
The data breach, which occurred on July 28, was identified and contained within hours, a TransUnion spokesperson told CNET. TransUnion is one of three credit bureaus — along with Equifax and Experian — that compile your financial activity into credit reports that are then used to create your credit scores. The credit bureau said it’s notifying people who may have been affected and sharing the actions the company is taking.
Don’t miss any of our unbiased tech content and lab-based reviews. Add CNET as a preferred Google source on Chrome.
Two separate state filings shed more details on the situation. A court filing in Maine shows that TransUnion acknowledged unauthorized access from a third-party application that stored personal customer data. While the notice to consumers says that no credit information was accessed, «limited personal information» was exposed. However, another filing from Texas states that names of individuals, Social Security numbers and birthdates were exposed in the breach.
The TransUnion spokesperson further clarified that the breach involved a third-party application serving its US consumer support operations but did not include its core credit database or credit reports. The bureau has engaged third-party cybersecurity experts for an independent forensics review.
The breach came after Google reported in June that hackers were using a modified version of a Salesforce-related app to steal vast stores of data, infiltrate other cloud systems and extort compromised companies. The same report named the cybercriminal hacking group ShinyHunters, which it said was linked to extortion demands to employees of the victim organizations.
Several global organizations have already been caught in a wave of Salesforce-linked attacks, according to BleepingComputer, including Google, Farmers Insurance, Allianz Life, Workday, Pandora, Cisco, Chanel and Qantas. Salesforce said social engineering, and not its platform, were to blame for the attacks.
«The Salesforce platform has not been compromised, and this issue is not due to any known vulnerability in our technology,» Salesforce said in a statement in August, adding that customers can mitigate the risk by enabling multi-factor authentication and closley managing connected applications.
Consumer rights law firm Wolf Haldenstein issued an alert on the breach and encouraged those who have received a notice and spot unusual activity on their credit report to reach out.
If you’re not sure if your private data was leaked or you haven’t received any communication from TransUnion, you can check by calling its Fraud Victim Assistance Department at 800-680-7289.
Even if you haven’t received a notice, if you’ve experienced unusual activity on your credit report, you can always freeze your credit for free, enable two-factor authentication or add a security key to your accounts.
Technologies
Wisconsin Reverses Decision to Ban VPNs in Age-Verification Bill
The law would have required websites to block VPN users from accessing «harmful material.»

Following a wave of criticism, Wisconsin lawmakers have decided not to include a ban on VPN services in their age-verification law, making its way through the state legislature.
Wisconsin Senate Bill 130 (and its sister Assembly Bill 105), introduced in March 2025, aims to prohibit businesses from «publishing or distributing material harmful to minors» unless there is a reasonable «method to verify the age of individuals attempting to access the website.»
One provision would have required businesses to bar people from accessing their sites via «a virtual private network system or virtual private network provider.»
A VPN lets you access the internet via an encrypted connection, enabling you to bypass firewalls and unblock geographically restricted websites and streaming content. While using a VPN, your IP address and physical location are masked, and your internet service provider doesn’t know which websites you visit.
Wisconsin state Sen. Van Wanggaard moved to delete that provision in the legislation, thereby releasing VPNs from any liability. The state assembly agreed to remove the VPN ban, and the bill now awaits Wisconsin Governor Tony Evers’s signature.
Rindala Alajaji, associate director of state affairs at the digital freedom nonprofit Electronic Frontier Foundation, says Wisconsin’s U-turn is «great news.»
«This shows the power of public advocacy and pushback,» Alajaji says. «Politicians heard the VPN users who shared their worries and fears, and the experts who explained how the ban wouldn’t work.»
Earlier this week, the EFF had written an open letter arguing that the draft laws did not «meaningfully advance the goal of keeping young people safe online.» The EFF said that blocking VPNs would harm many groups that rely on that software for private and secure internet connections, including «businesses, universities, journalists and ordinary citizens,» and that «many law enforcement professionals, veterans and small business owners rely on VPNs to safely use the internet.»
More from CNET: Best VPN Service for 2026: VPNs Tested by Our Experts
VPNs can also help you get around age-verification laws — for instance, if you live in a state or country that requires age verification to access certain material, you can use a VPN to make it look like you live elsewhere, thereby gaining access to that material. As age-restriction laws increase around the US, VPN use has also increased. However, many people are using free VPNs, which are fertile ground for cybercriminals.
In its letter to Wisconsin lawmakers prior to the reversal, the EFF argued that it is «unworkable» to require websites to block VPN users from accessing adult content. The EFF said such sites cannot «reliably determine» where a VPN customer lives — it could be any US state or even other countries.
«As a result, covered websites would face an impossible choice: either block all VPN users everywhere, disrupting access for millions of people nationwide, or cease offering services in Wisconsin altogether,» the EFF wrote.
Wisconsin is not the only state to consider VPN bans to prevent access to adult material. Last year, Michigan introduced the Anticorruption of Public Morals Act, which would ban all use of VPNs. If passed, it would force ISPs to detect and block VPN usage and also ban the sale of VPNs in the state. Fines could reach $500,000.
Technologies
Today’s NYT Strands Hints, Answers and Help for Feb. 21 #720
Here are hints and answers for the NYT Strands puzzle for Feb. 21, No. 720.
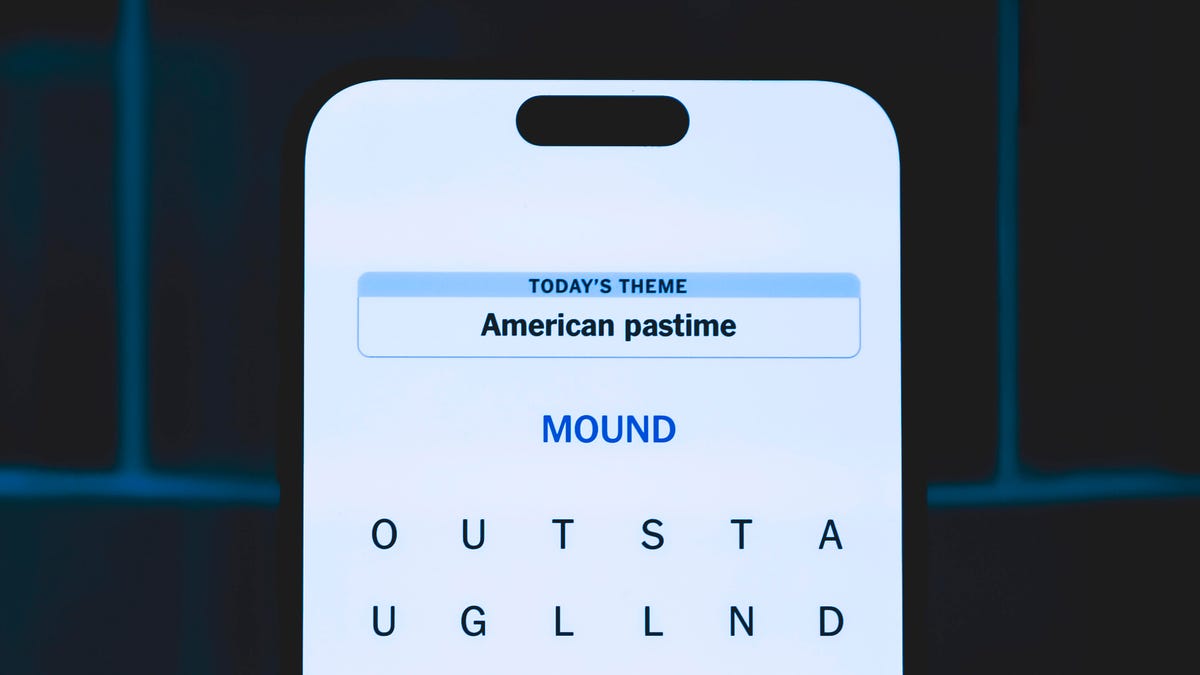
Looking for the most recent Strands answer? Click here for our daily Strands hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle, Connections and Connections: Sports Edition puzzles.
Today’s NYT Strands puzzle might be easy for those who pursue a certain hobby. Some of the answers are difficult to unscramble, so if you need hints and answers, read on.
I go into depth about the rules for Strands in this story.
If you’re looking for today’s Wordle, Connections and Mini Crossword answers, you can visit CNET’s NYT puzzle hints page.
Read more: NYT Connections Turns 1: These Are the 5 Toughest Puzzles So Far
Hint for today’s Strands puzzle
Today’s Strands theme is: The beer necessities.
If that doesn’t help you, here’s a clue: Cheers!
Clue words to unlock in-game hints
Your goal is to find hidden words that fit the puzzle’s theme. If you’re stuck, find any words you can. Every time you find three words of four letters or more, Strands will reveal one of the theme words. These are the words I used to get those hints but any words of four or more letters that you find will work:
- MALE, TREAT, STEAM, TEAM, MOVE, LOVE, ROVE, ROVER, SPEAR, PEAR
Answers for today’s Strands puzzle
These are the answers that tie into the theme. The goal of the puzzle is to find them all, including the spangram, a theme word that reaches from one side of the puzzle to the other. When you have all of them (I originally thought there were always eight but learned that the number can vary), every letter on the board will be used. Here are the nonspangram answers:
- HOPS, WATER, MALT, YEAST, BARLEY, SUGAR, WHEAT, FLAVOR
Today’s Strands spangram
Today’s Strands spangram is HOMEBREW. To find it, start with the H that’s three letters to the right on the top row, and wind down.
Technologies
Today’s NYT Connections Hints, Answers and Help for Feb. 21, #986
Here are some hints and the answers for the NYT Connections puzzle for Feb. 21 #986.

Looking for the most recent Connections answers? Click here for today’s Connections hints, as well as our daily answers and hints for The New York Times Mini Crossword, Wordle, Connections: Sports Edition and Strands puzzles.
Today’s NYT Connections puzzle features another of those purple categories where you need to look for hidden words inside of other words. It can be a real stumper. Read on for clues and today’s Connections answers.
The Times has a Connections Bot, like the one for Wordle. Go there after you play to receive a numeric score and to have the program analyze your answers. Players who are registered with the Times Games section can now nerd out by following their progress, including the number of puzzles completed, win rate, number of times they nabbed a perfect score and their win streak.
Read more: Hints, Tips and Strategies to Help You Win at NYT Connections Every Time
Hints for today’s Connections groups
Here are four hints for the groupings in today’s Connections puzzle, ranked from the easiest yellow group to the tough (and sometimes bizarre) purple group.
Yellow group hint: Rookies don’t have this.
Green group hint: Call the roll.
Blue group hint: How’d you do today?
Purple group hint: Vroom-vroom, but with a twist.
Answers for today’s Connections groups
Yellow group: Experience.
Green group: Attendance status.
Blue group: Commentary about your Connections results.
Purple group: Car brands plus two letters.
Read more: Wordle Cheat Sheet: Here Are the Most Popular Letters Used in English Words
What are today’s Connections answers?
The yellow words in today’s Connections
The theme is experience. The four answers are background, history, life and past.
The green words in today’s Connections
The theme is attendance status. The four answers are absent, excused, late and present.
The blue words in today’s Connections
The theme is commentary about your Connections results. The four answers are great, perfect, phew and solid.
The purple words in today’s Connections
The theme is car brands plus two letters. The four answers are audits (Audi), Dodgers (Dodge), Infinitive (Infiniti) and Minion (Mini).
-

 Technologies3 года ago
Technologies3 года agoTech Companies Need to Be Held Accountable for Security, Experts Say
-

 Technologies3 года ago
Technologies3 года agoBest Handheld Game Console in 2023
-

 Technologies3 года ago
Technologies3 года agoTighten Up Your VR Game With the Best Head Straps for Quest 2
-

 Technologies4 года ago
Technologies4 года agoBlack Friday 2021: The best deals on TVs, headphones, kitchenware, and more
-

 Technologies5 лет ago
Technologies5 лет agoGoogle to require vaccinations as Silicon Valley rethinks return-to-office policies
-

 Technologies5 лет ago
Technologies5 лет agoVerum, Wickr and Threema: next generation secured messengers
-

 Technologies4 года ago
Technologies4 года agoOlivia Harlan Dekker for Verum Messenger
-

 Technologies4 года ago
Technologies4 года agoiPhone 13 event: How to watch Apple’s big announcement tomorrow
